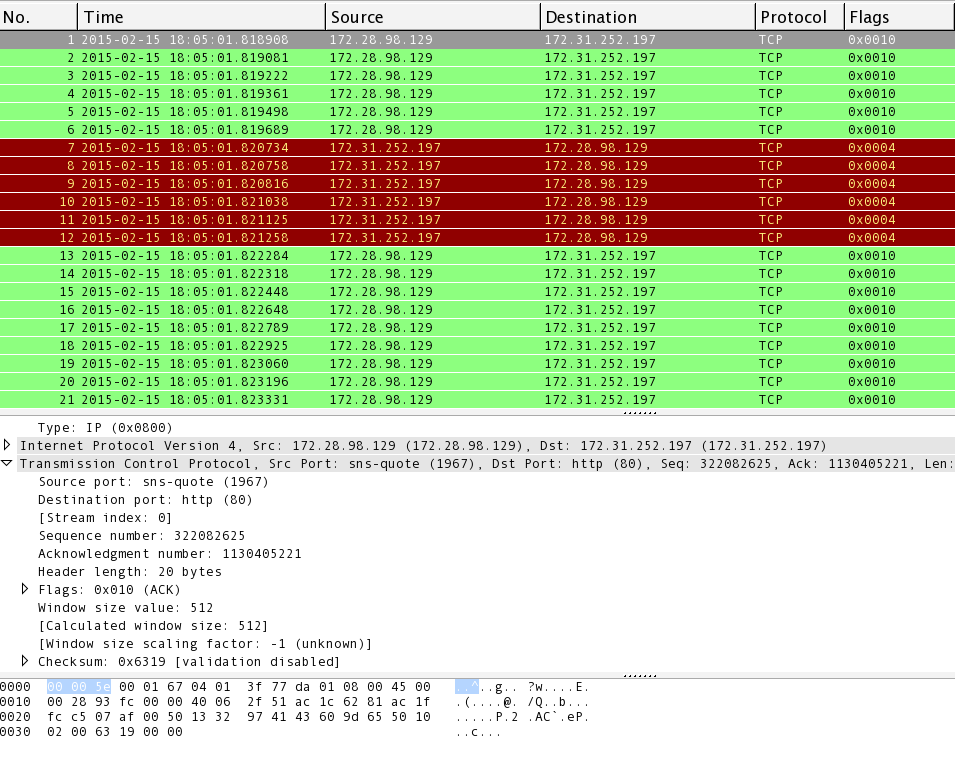
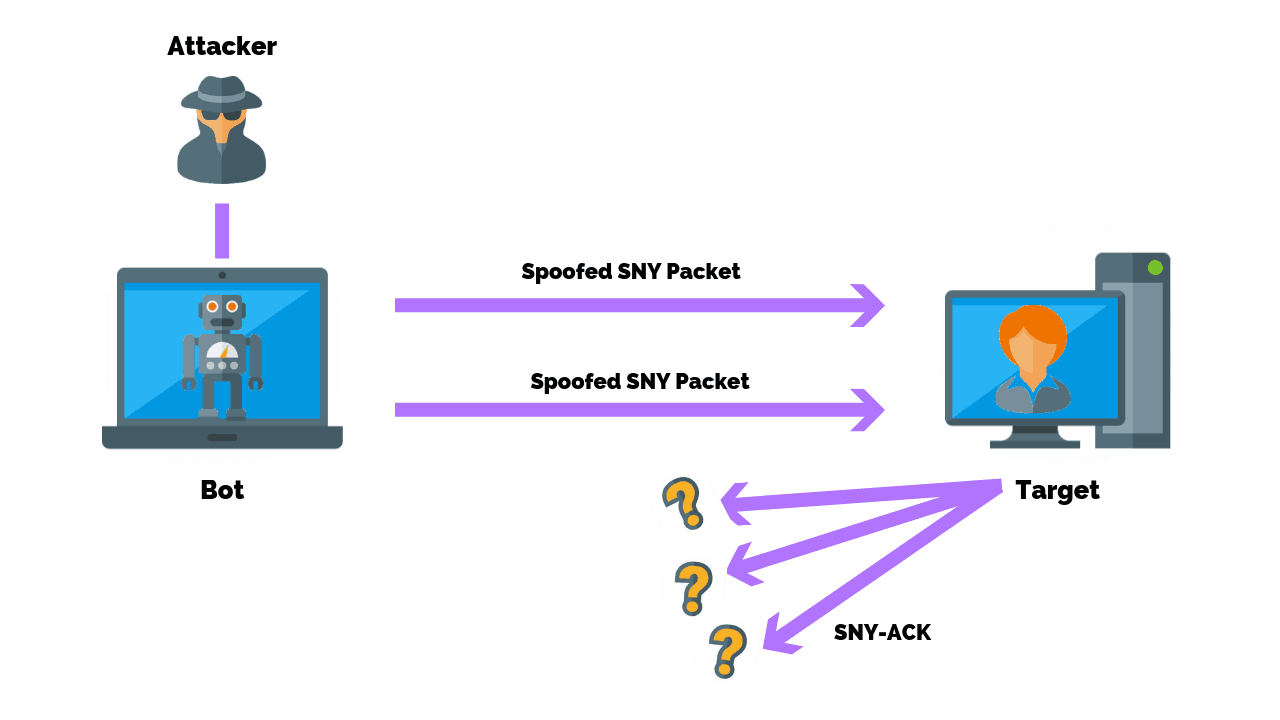
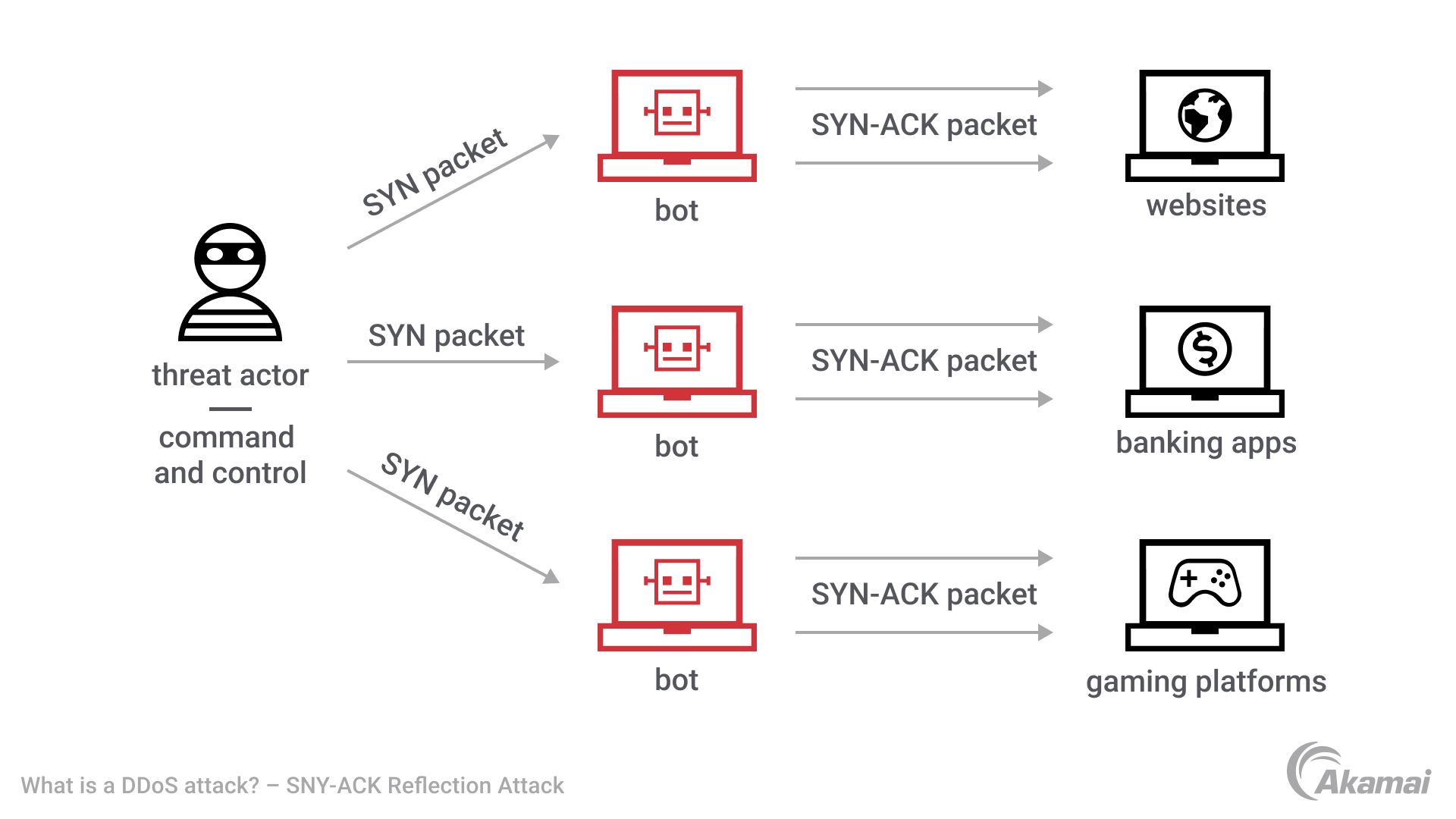
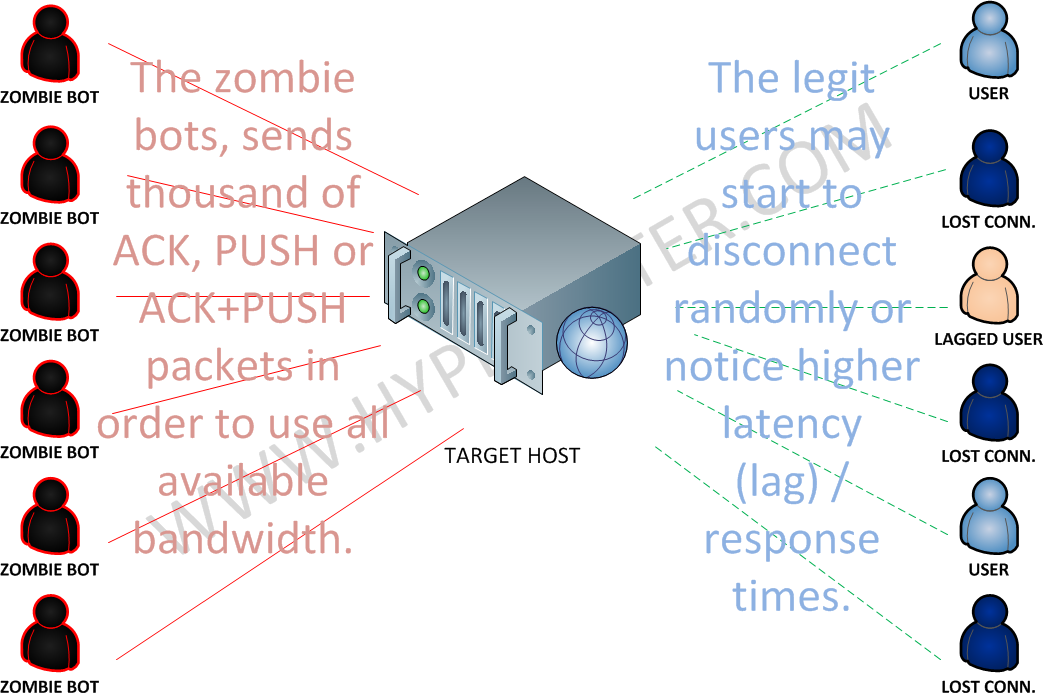
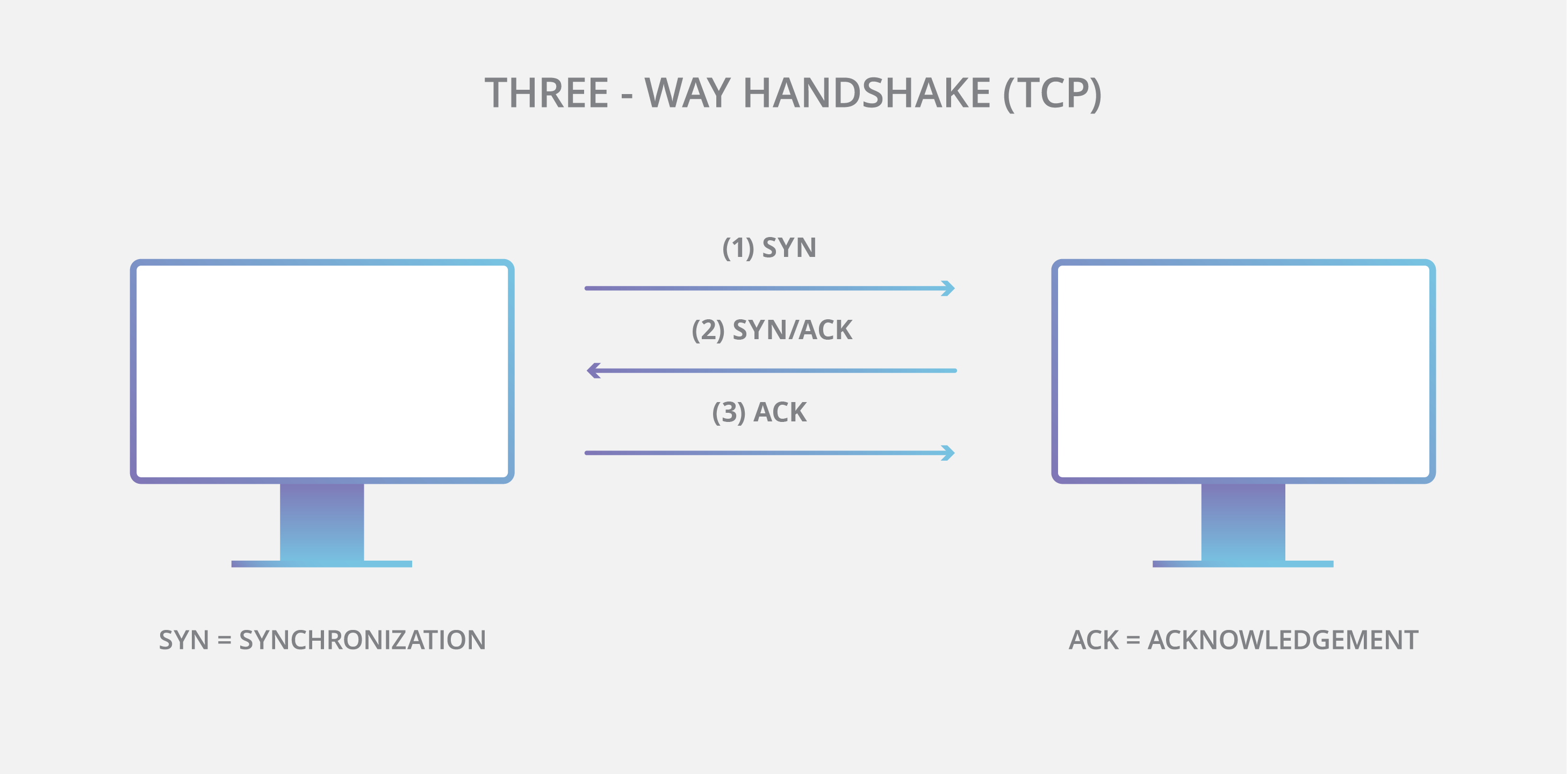
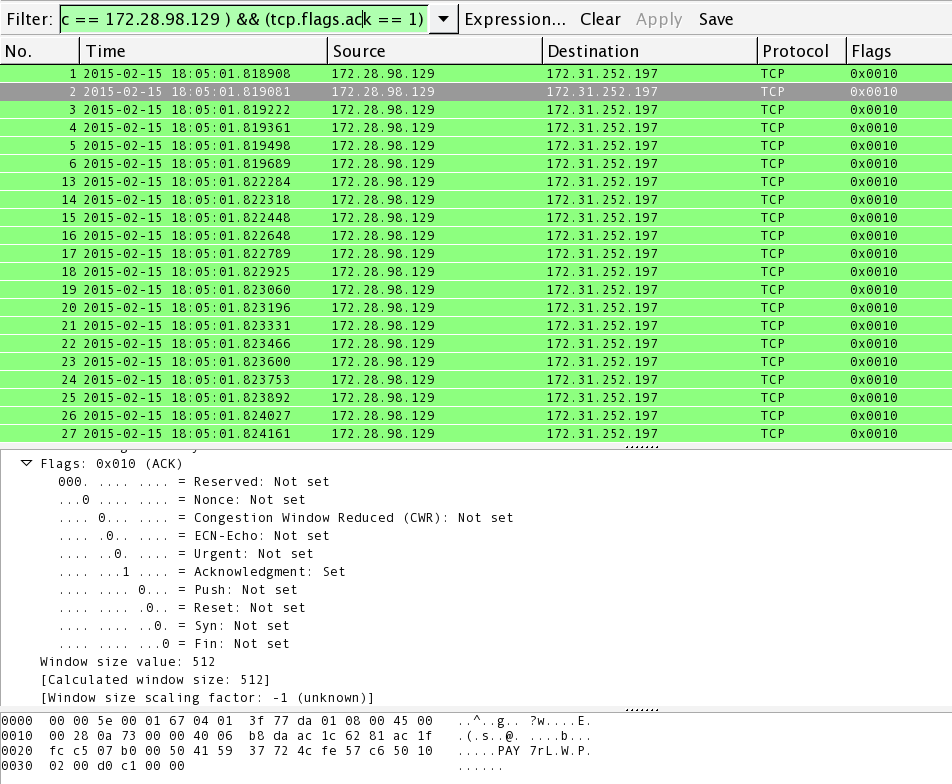
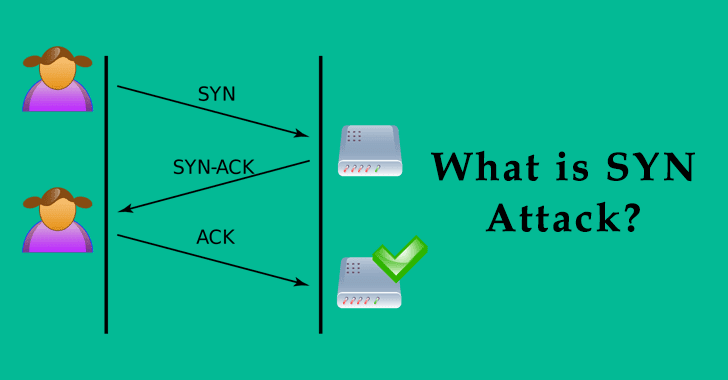
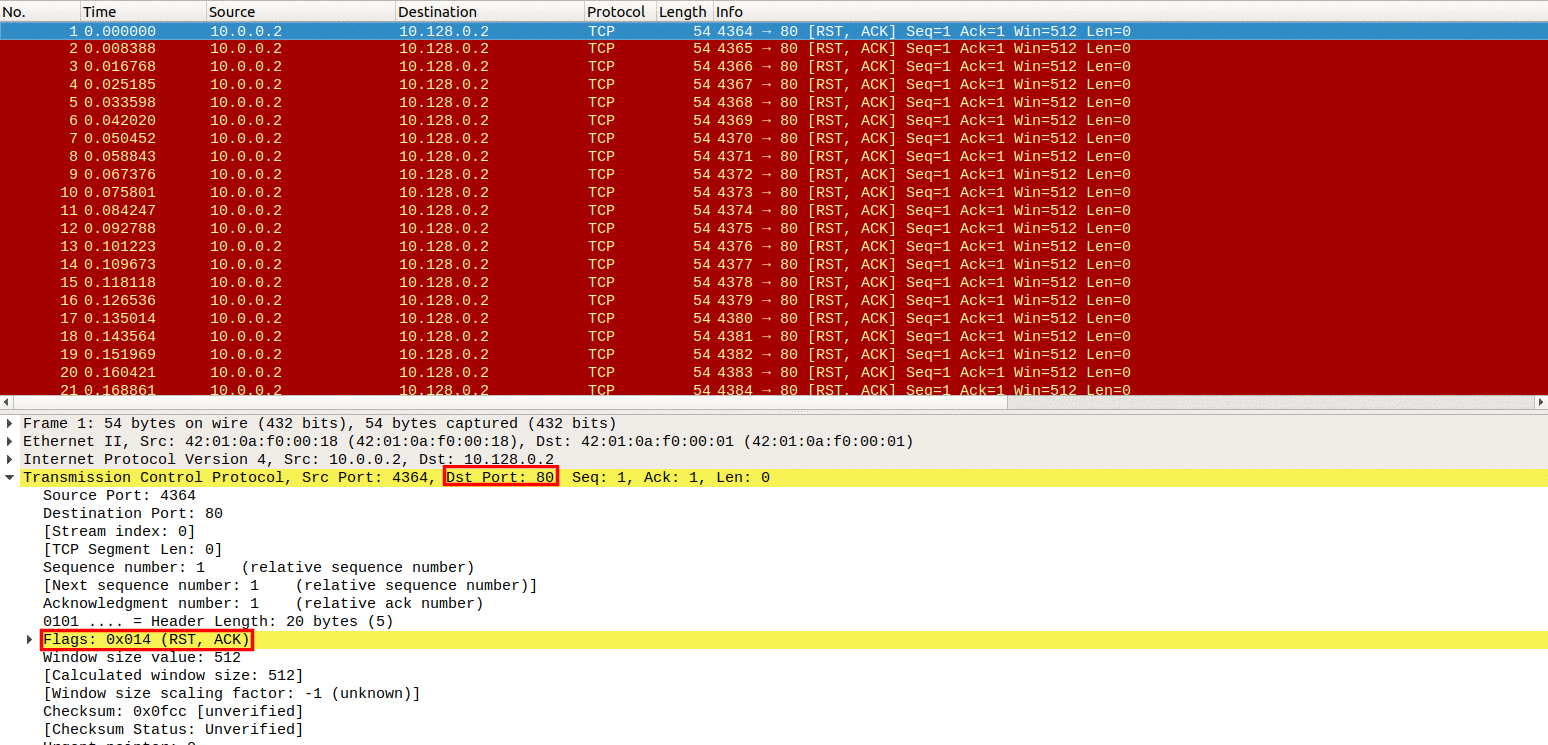
Detecting SYN flooding attacks based on traffic prediction - Wang - 2012 - Security and Communication Networks - Wiley Online Library
![PDF] Analysis and Review of TCP SYN Flood Attack on Network with Its Detection and Performance Metrics | Semantic Scholar PDF] Analysis and Review of TCP SYN Flood Attack on Network with Its Detection and Performance Metrics | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/0f160f37587f25c9f803209d807edf5648e381cd/3-Figure7-1.png)
PDF] Analysis and Review of TCP SYN Flood Attack on Network with Its Detection and Performance Metrics | Semantic Scholar