How to aggregate and visualize AWS Health events using AWS Organizations and Amazon Elasticsearch Service | AWS Cloud Operations & Migrations Blog

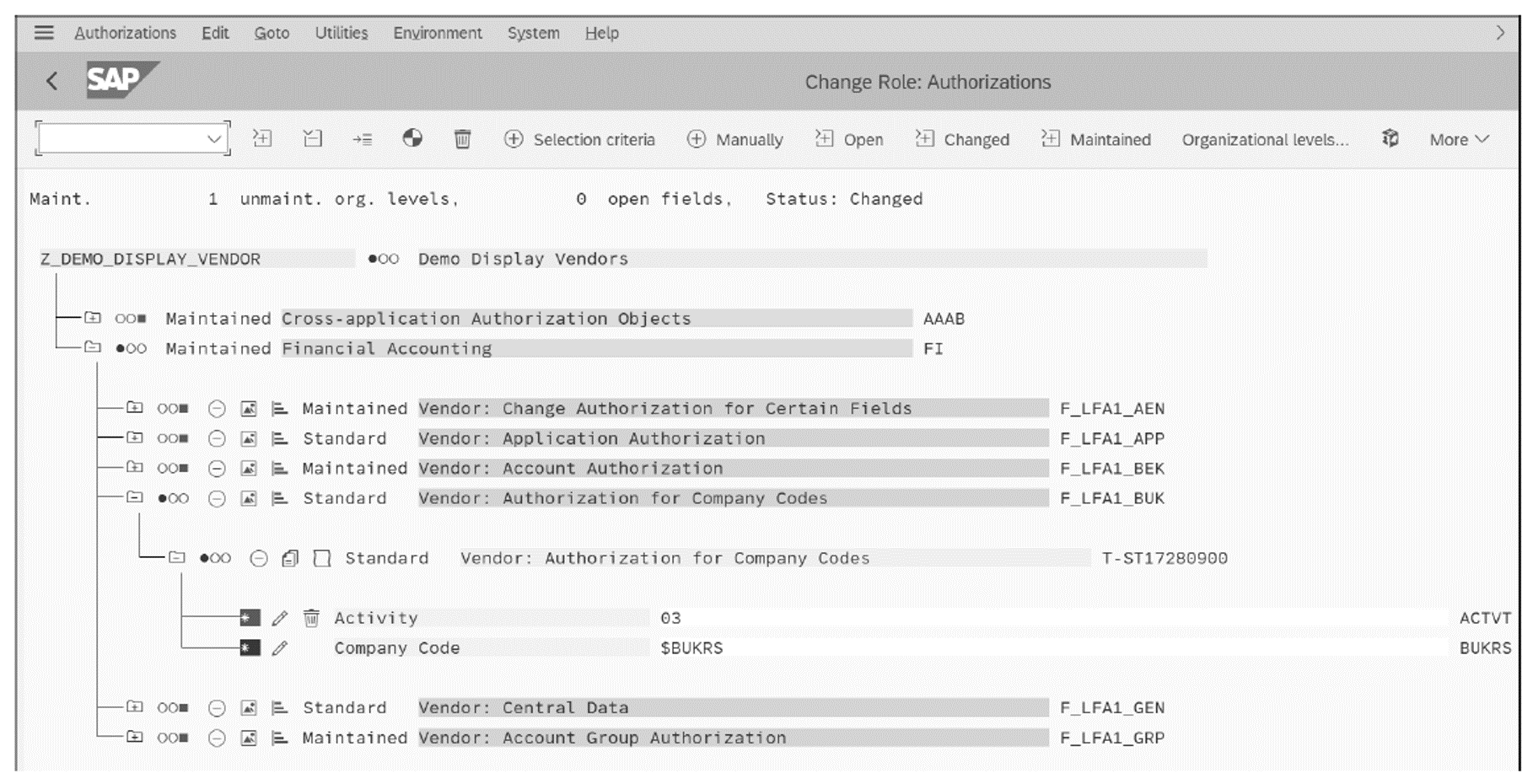
Listing all User name with respective assigned Roles in SAP system and exporting the data to local file | SAP Blogs

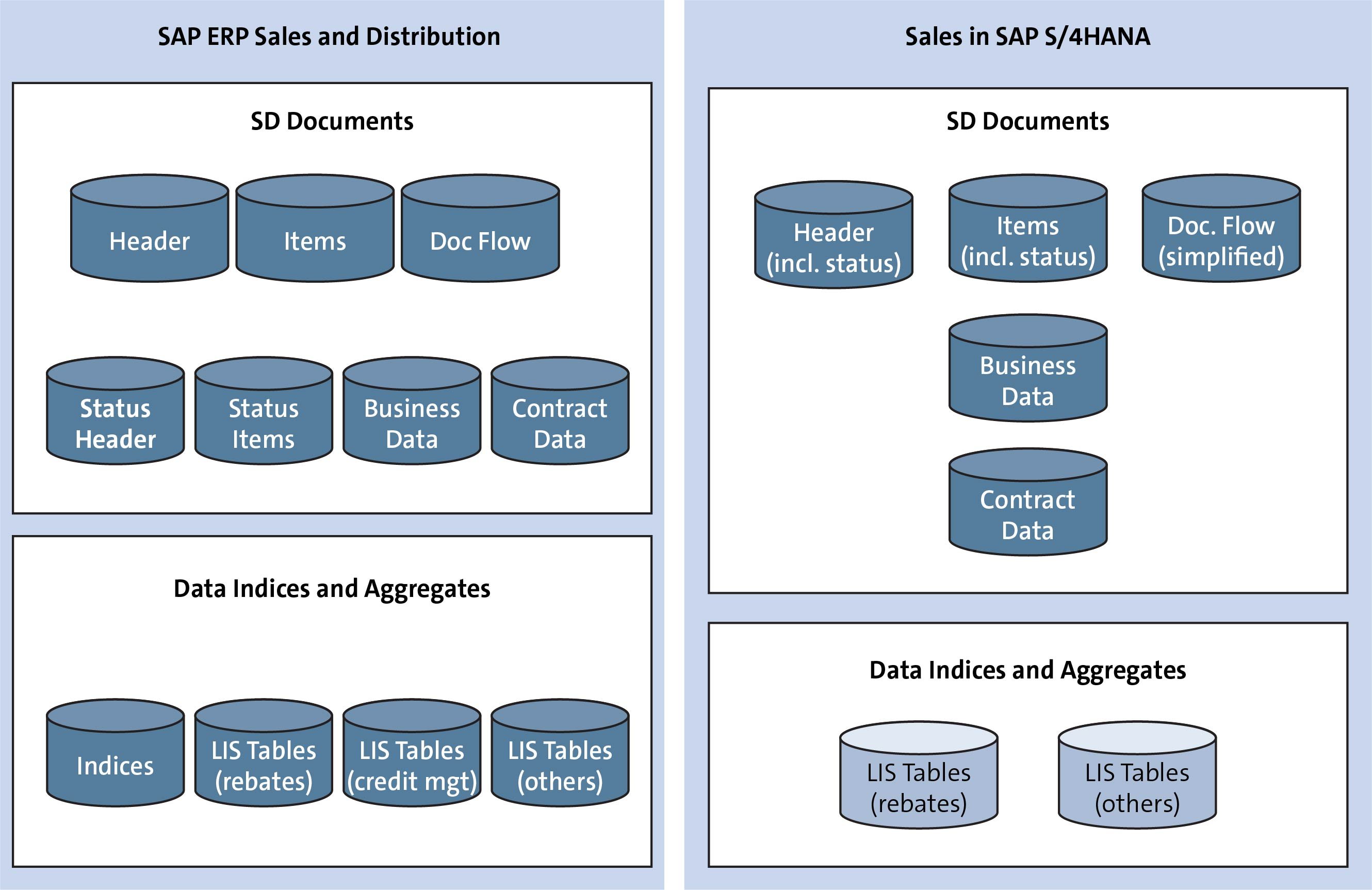
Build a near real-time data aggregation pipeline using a serverless, event-driven architecture | AWS Database Blog