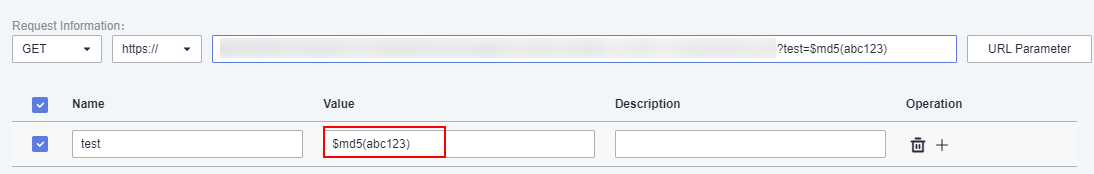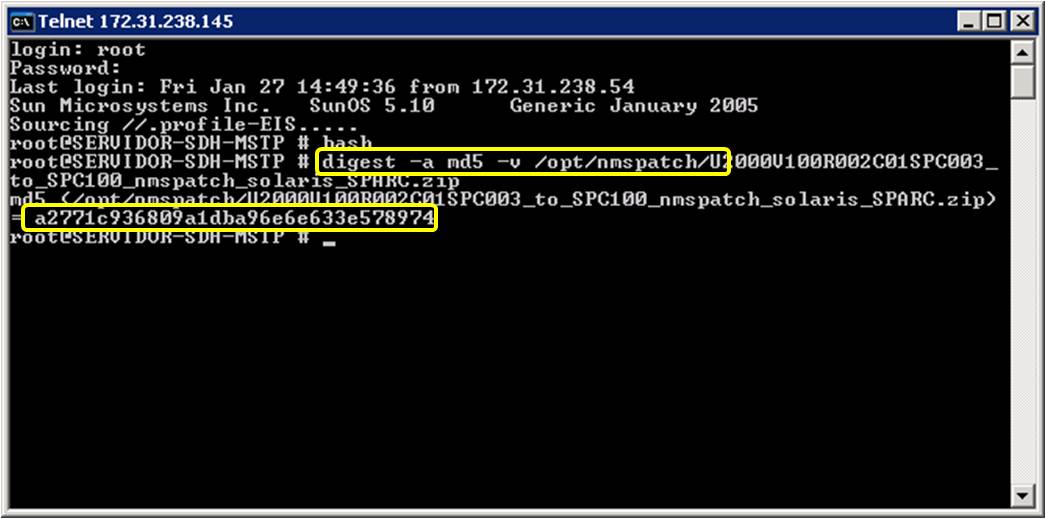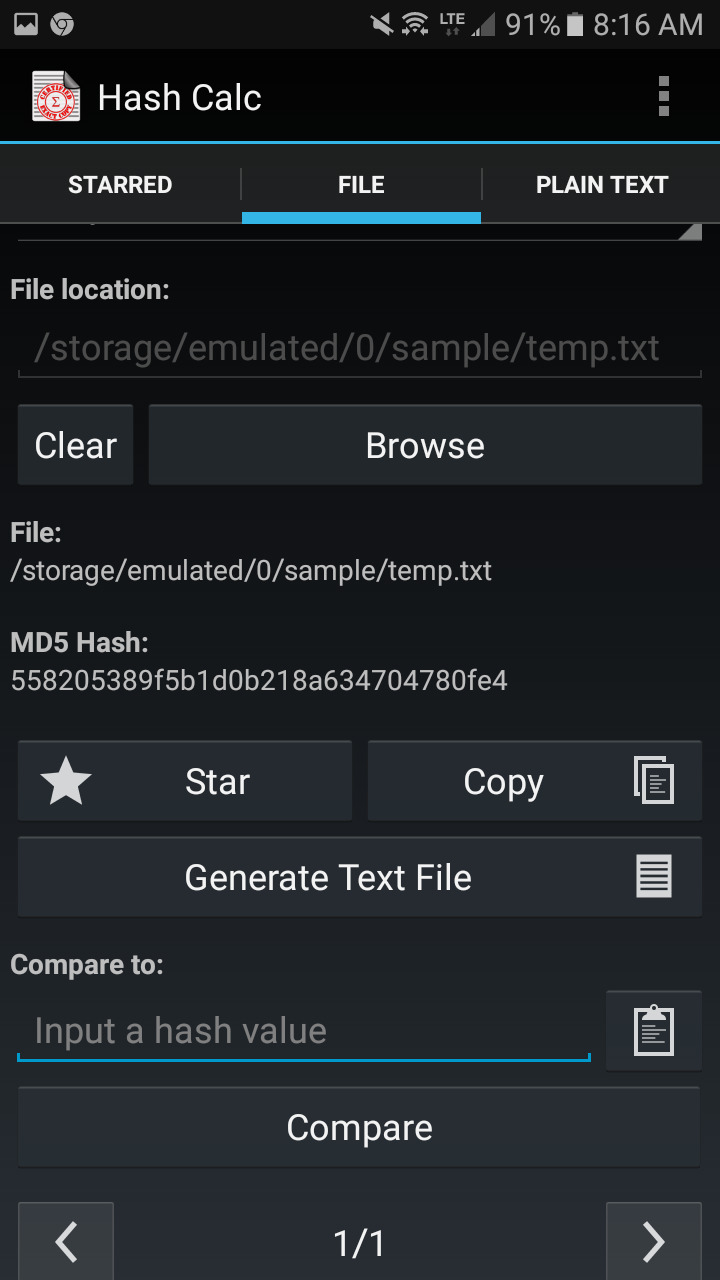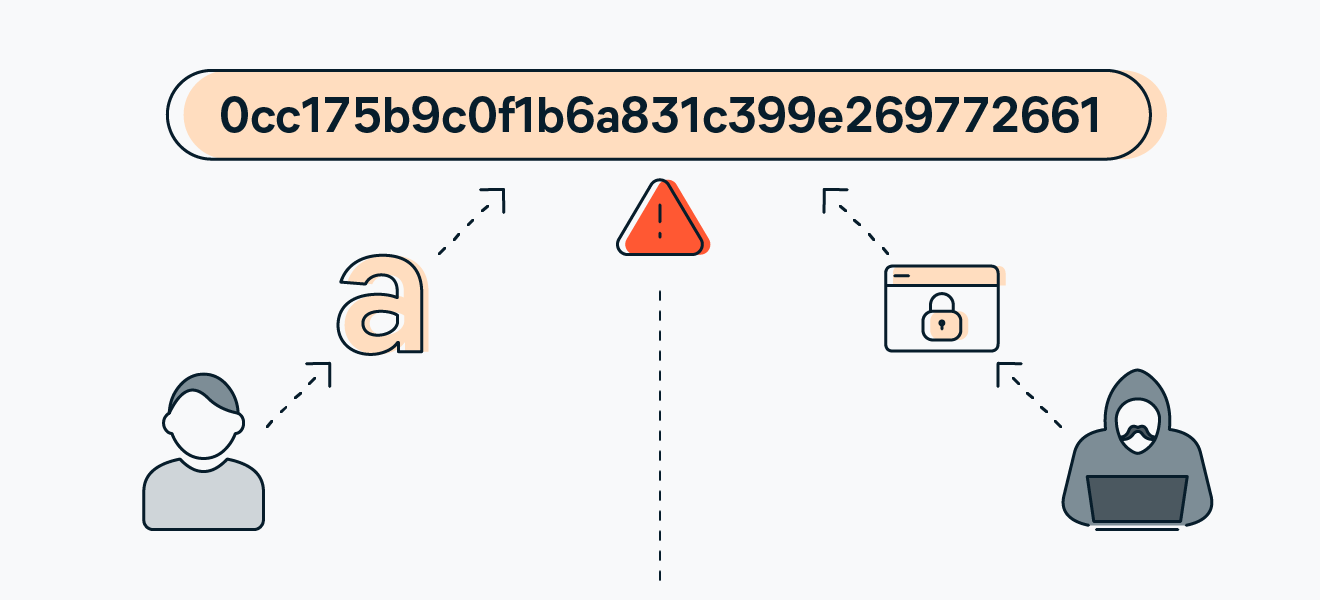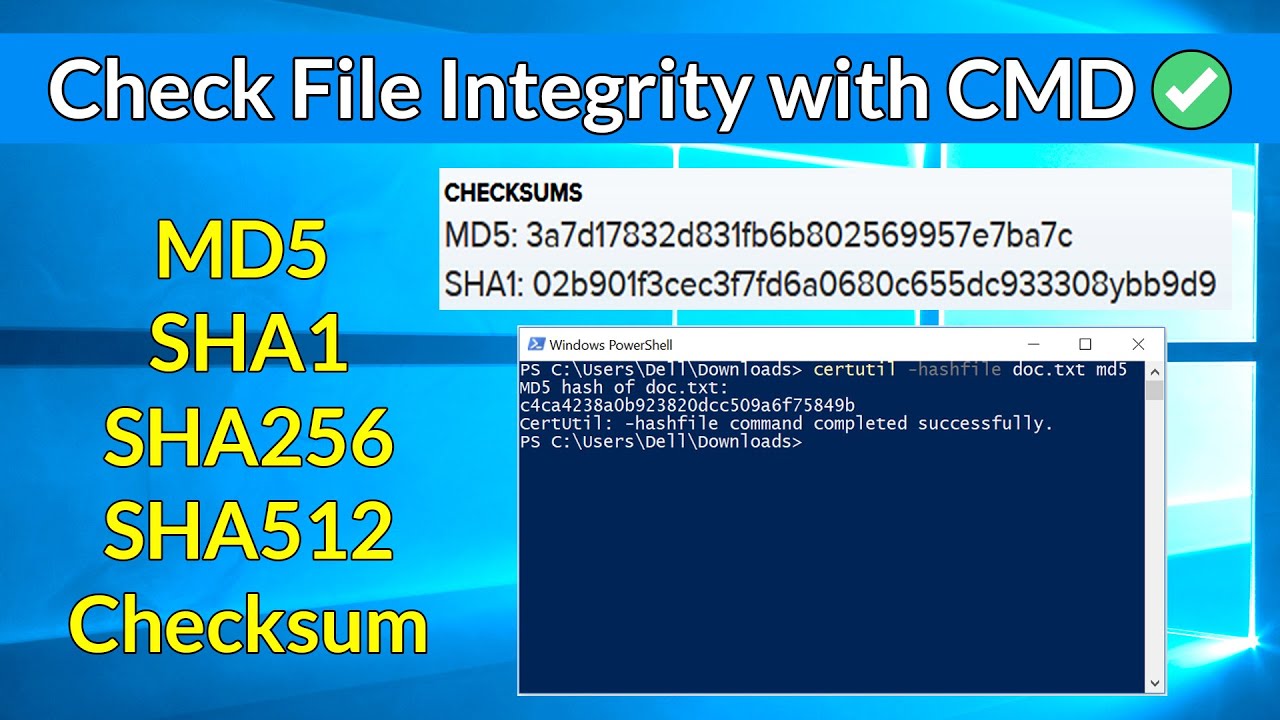
How to quickly verify MD5, SHA1 and SHA2 (256, 384, 512) Checksum in Windows using Command Prompt - YouTube

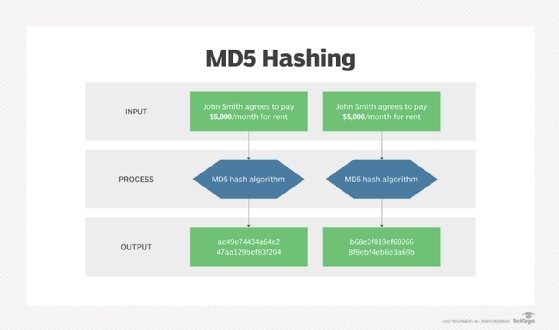
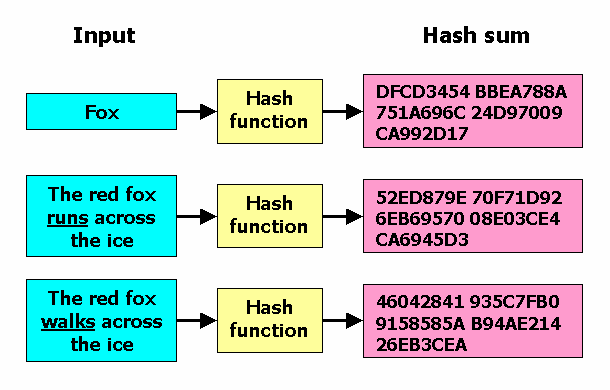
How to compute MD5 Hash (Message-Digest algorithm 5) using Cryptography? - .Net Core | MVC | HTML Agility Pack | SQL | Technology Crowds

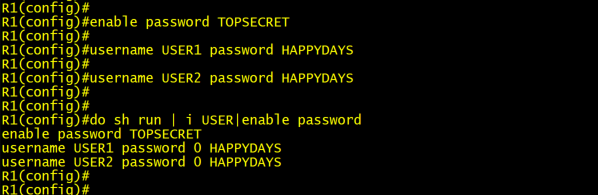
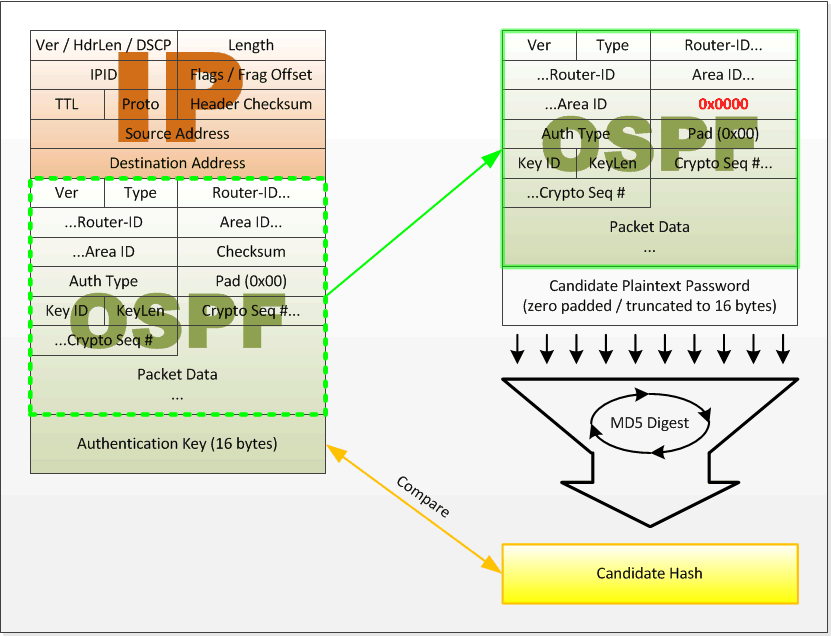
Router generates and checks the MD5 digest of every segment sent on the TCP connection Router authenticates the source of each routing update packet that it receives - Cisco Internetworks