![System Security Configuration Guide for Cisco NCS 540 Series Routers, IOS XR Release 7.3.x - Understanding MACsec Encryption [Cisco Network Convergence System 540 Series Routers] - Cisco System Security Configuration Guide for Cisco NCS 540 Series Routers, IOS XR Release 7.3.x - Understanding MACsec Encryption [Cisco Network Convergence System 540 Series Routers] - Cisco](https://www.cisco.com/c/dam/en/us/td/i/300001-400000/360001-370000/364001-365000/364757.eps/_jcr_content/renditions/364757.jpg)
System Security Configuration Guide for Cisco NCS 540 Series Routers, IOS XR Release 7.3.x - Understanding MACsec Encryption [Cisco Network Convergence System 540 Series Routers] - Cisco

Amazon.com: GL.iNet GL-SFT1200 (Opal) Secure Travel WiFi Router – AC1200 Dual Band Gigabit Ethernet Wireless Internet Router | IPv6 | USB 2.0 | MU-MIMO | DDR3 |128MB Ram | Repeater Bridge
![Cisco Catalyst 9800 Series Wireless Controller Software Configuration Guide, Cisco IOS XE Gibraltar 16.10.x - Encrypted Traffic Analytics [Cisco Catalyst 9800 Series Wireless Controllers] - Cisco Cisco Catalyst 9800 Series Wireless Controller Software Configuration Guide, Cisco IOS XE Gibraltar 16.10.x - Encrypted Traffic Analytics [Cisco Catalyst 9800 Series Wireless Controllers] - Cisco](https://www.cisco.com/c/dam/en/us/td/i/300001-400000/350001-360000/355001-356000/355716.jpg)
Cisco Catalyst 9800 Series Wireless Controller Software Configuration Guide, Cisco IOS XE Gibraltar 16.10.x - Encrypted Traffic Analytics [Cisco Catalyst 9800 Series Wireless Controllers] - Cisco
![Security Configuration Guide for vEdge Routers, Cisco SD-WAN Releases 19.1, 19.2, and 19.3 - Security Overview [Cisco SD-WAN] - Cisco Security Configuration Guide for vEdge Routers, Cisco SD-WAN Releases 19.1, 19.2, and 19.3 - Security Overview [Cisco SD-WAN] - Cisco](https://www.cisco.com/c/dam/en/us/td/i/300001-400000/360001-370000/368001-369000/368450.jpg)
Security Configuration Guide for vEdge Routers, Cisco SD-WAN Releases 19.1, 19.2, and 19.3 - Security Overview [Cisco SD-WAN] - Cisco
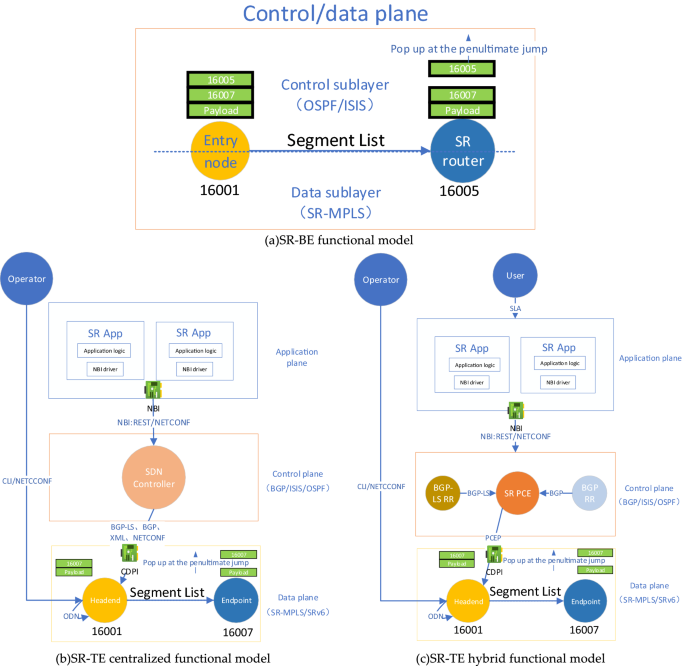
A data plane security model of segmented routing based on SDP trust enhancement architecture | Scientific Reports
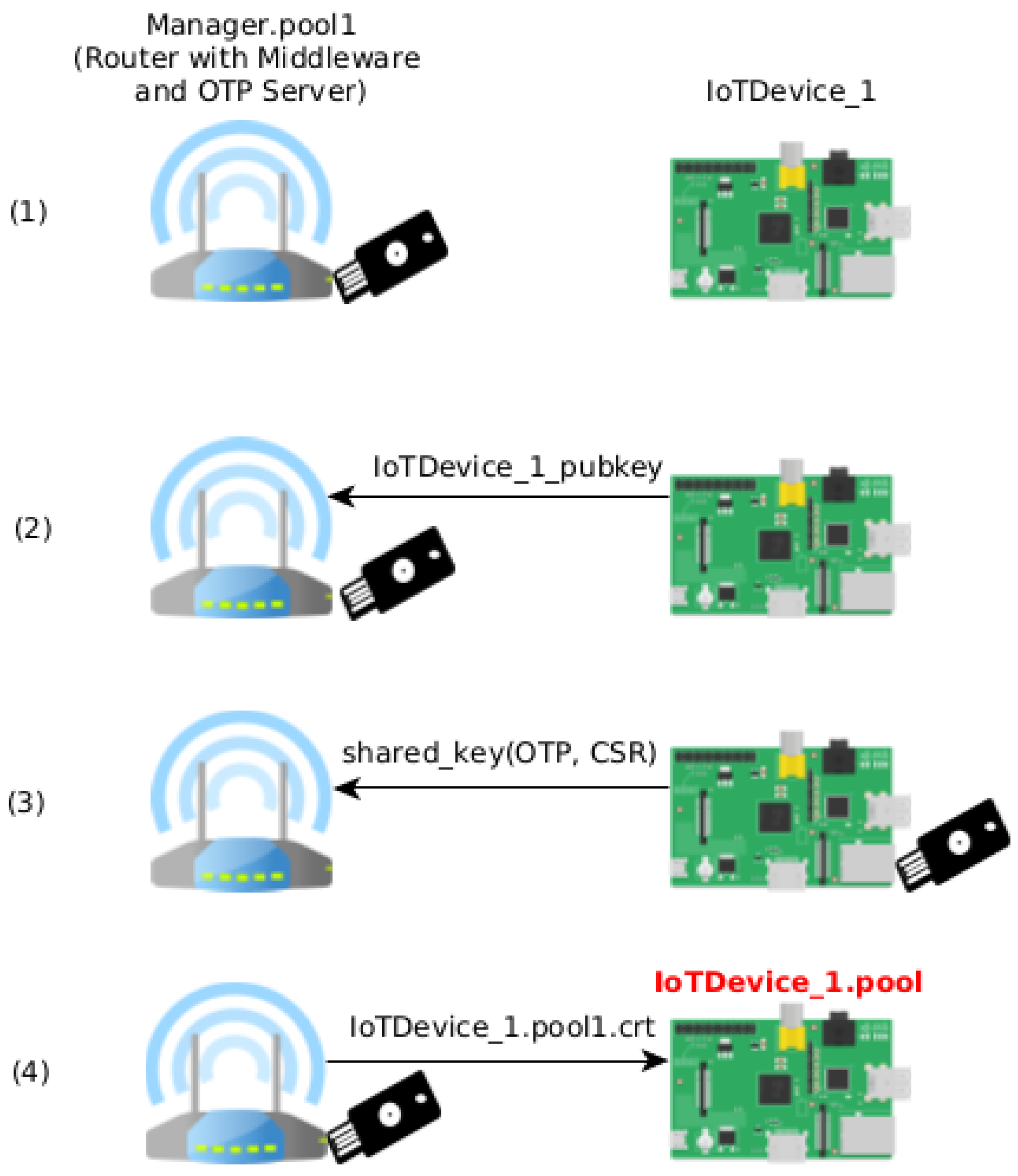
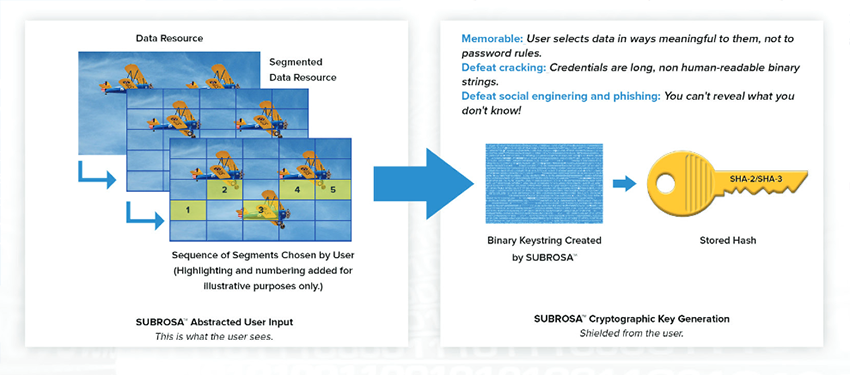
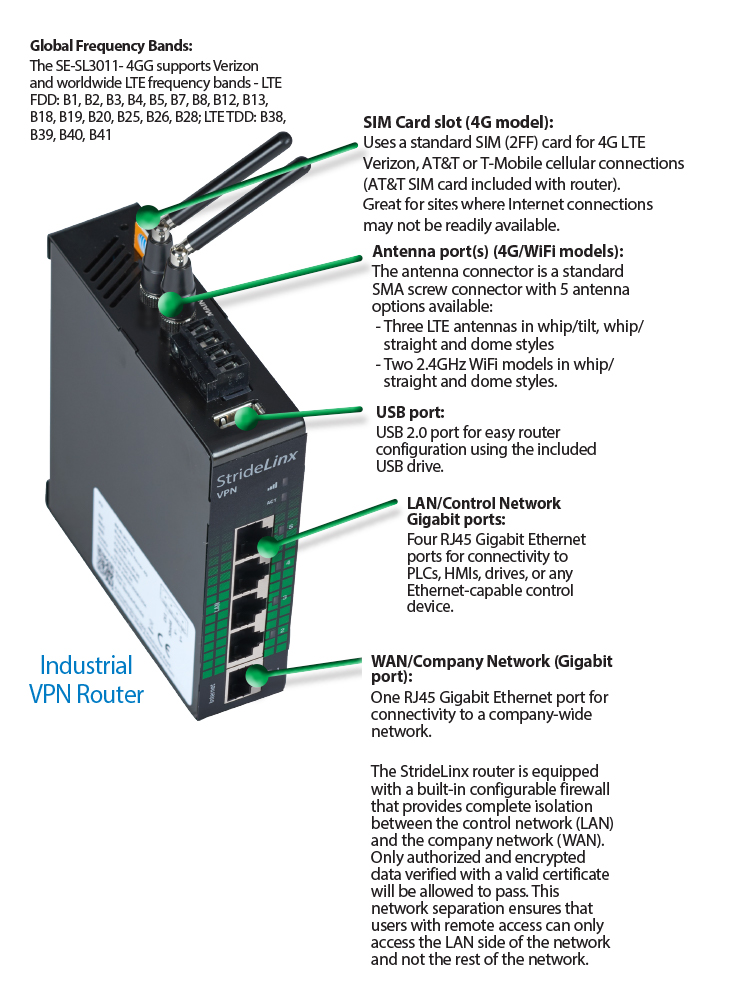






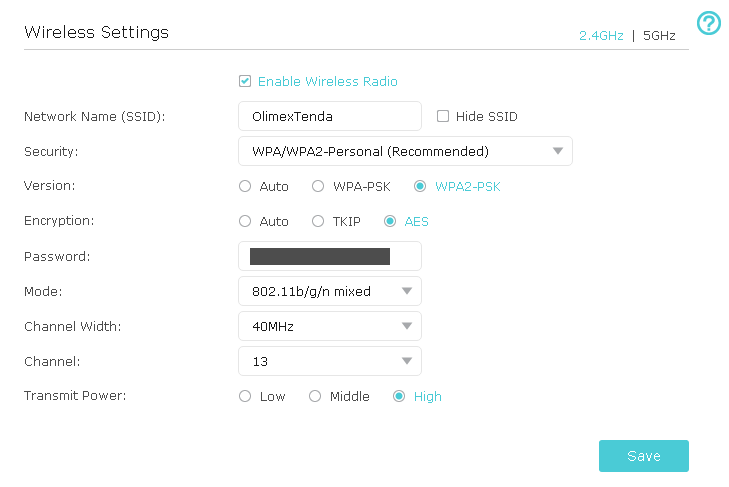



:max_bytes(150000):strip_icc()/comtrend-wireless-security-settings-5c47a3a646e0fb00019eb742.png)