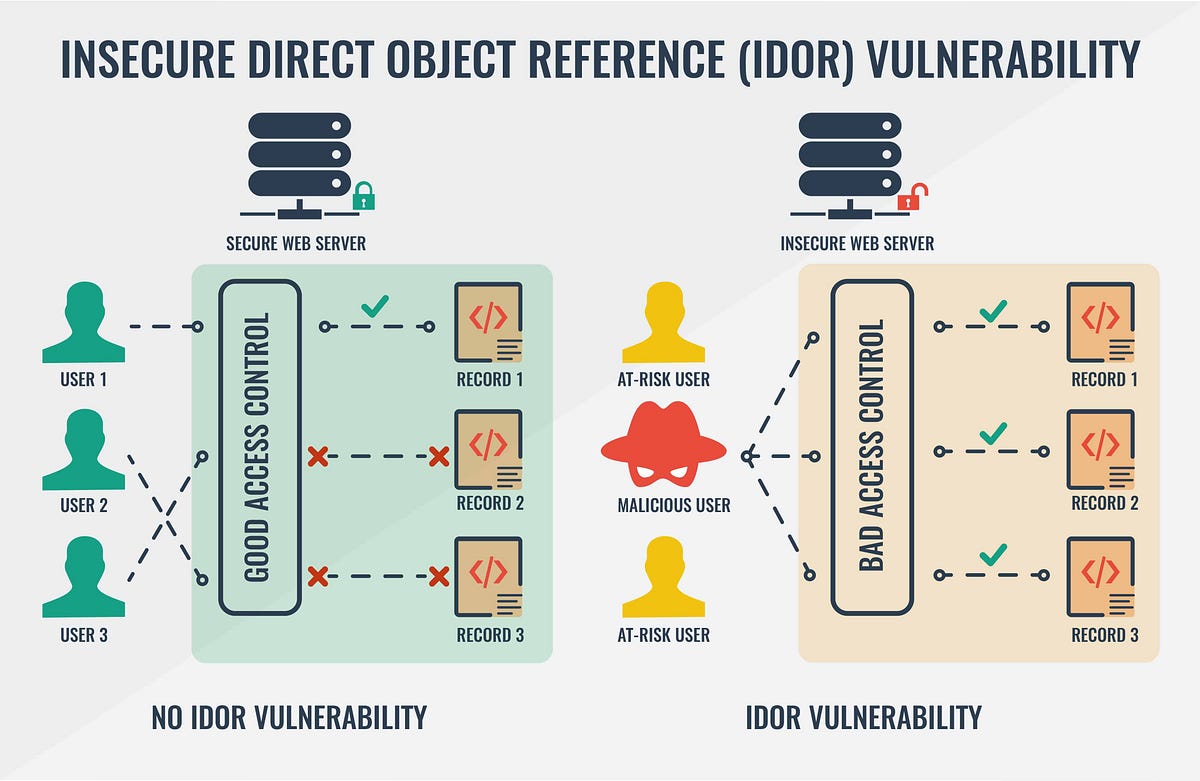
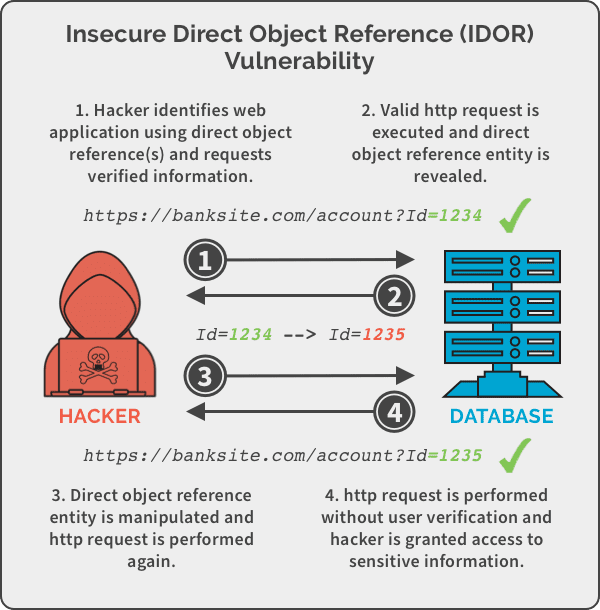
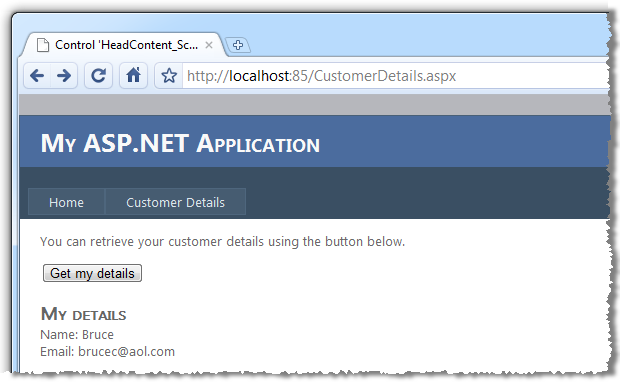
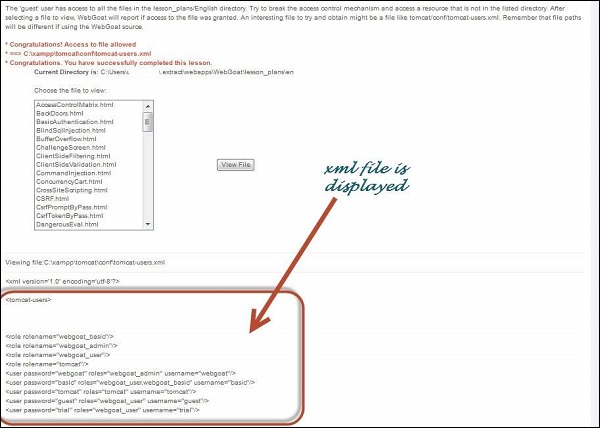
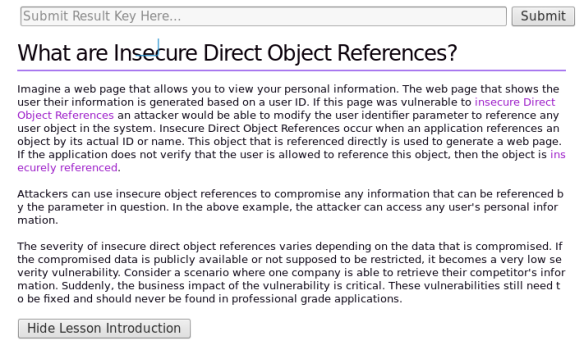
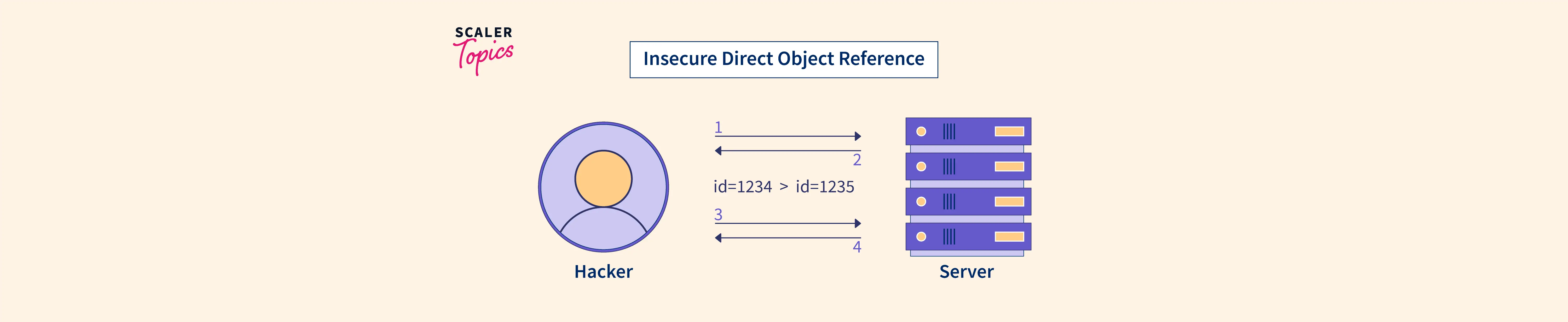
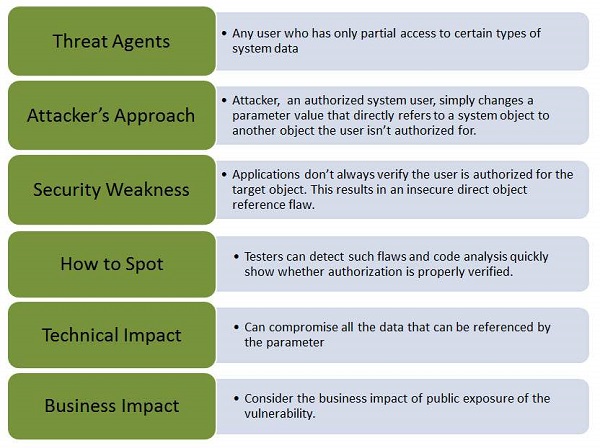
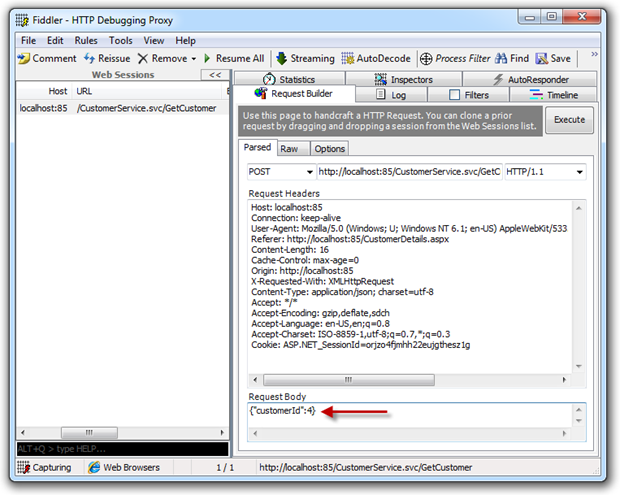
Extracting data using Insecure Direct Object Reference (IDOR) flaws | Hands-On Application Penetration Testing with Burp Suite
OWASP Security Shepherd Project - Insecure Direct Object Reference 2 (Insecure Direct Object Reference Challenge)

Insecure Direct Object Reference (IDOR) in GraphQL API which has an impact on Takeover Vouchers that have been used can still be reused | by Aidil Arief | Medium