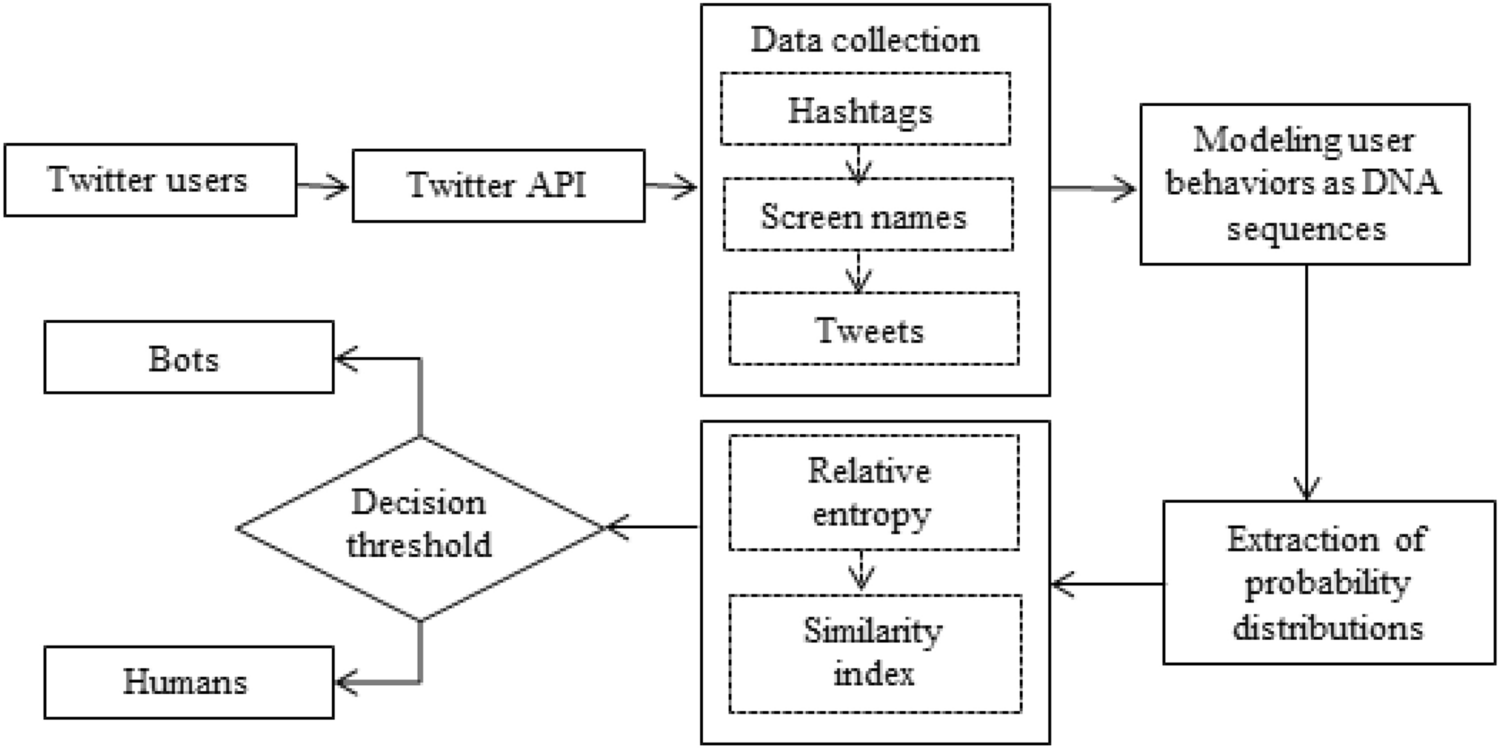
DNA-influenced automated behavior detection on twitter through relative entropy | Scientific Reports

Mathematics | Free Full-Text | State-Based Differential Privacy Verification and Enforcement for Probabilistic Automata

The Moving Object Detection and Research Effects of Noise on Images Based on Cellular Automata With a Hexagonal Coating Form and Radon Transform: Computer Science & IT Book Chapter | IGI Global
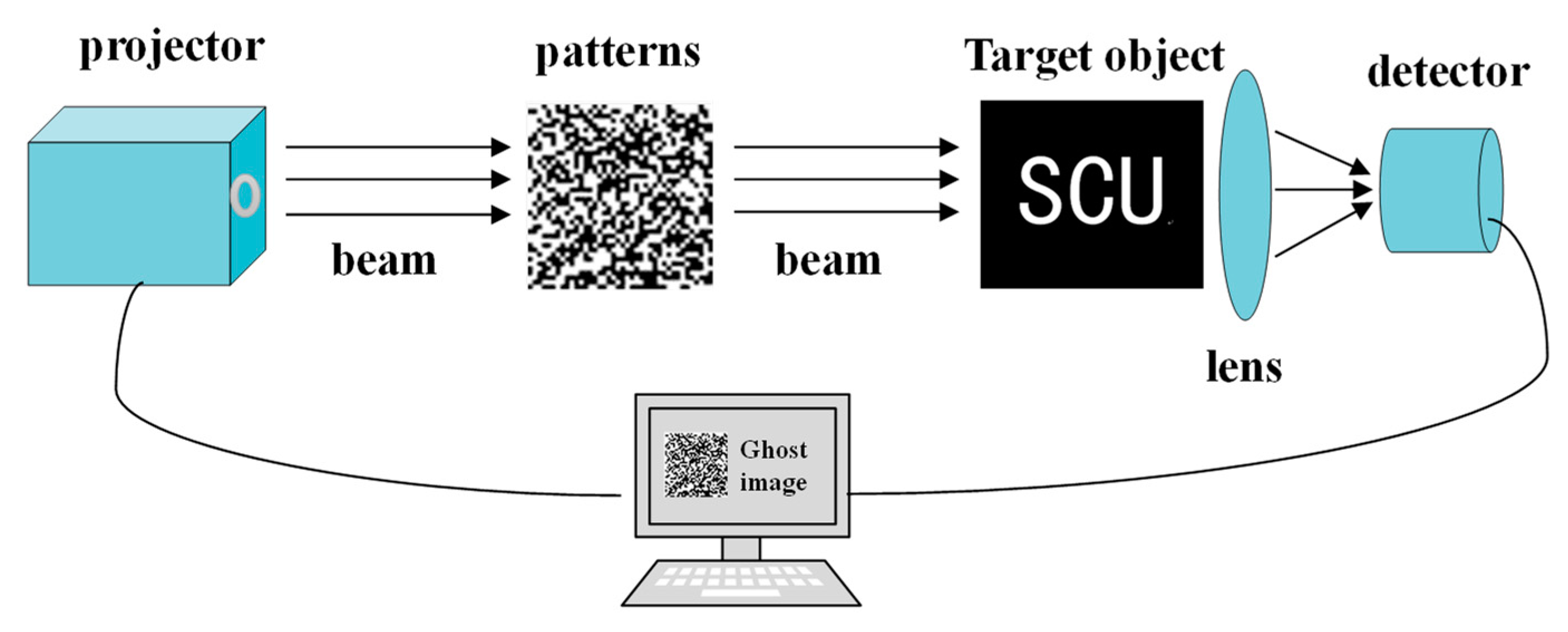
Symmetry | Free Full-Text | 3D Copyright Protection Based on Binarized Computational Ghost Imaging Encryption and Cellular Automata Transform
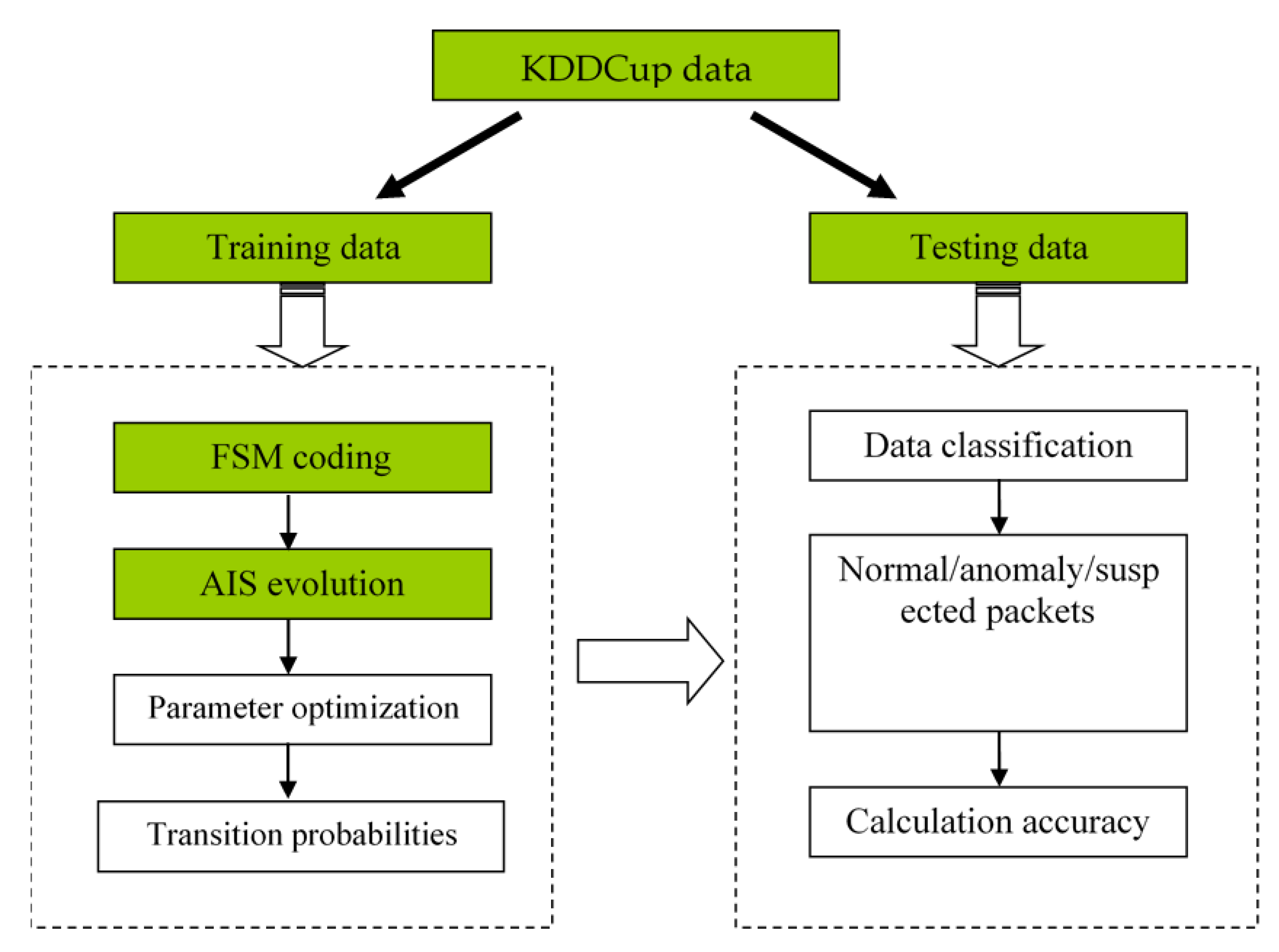
Applied Sciences | Free Full-Text | Detecting Mixed-Type Intrusion in High Adaptability Using Artificial Immune System and Parallelized Automata

The proposed model including five main steps: Human detection, Pose... | Download Scientific Diagram
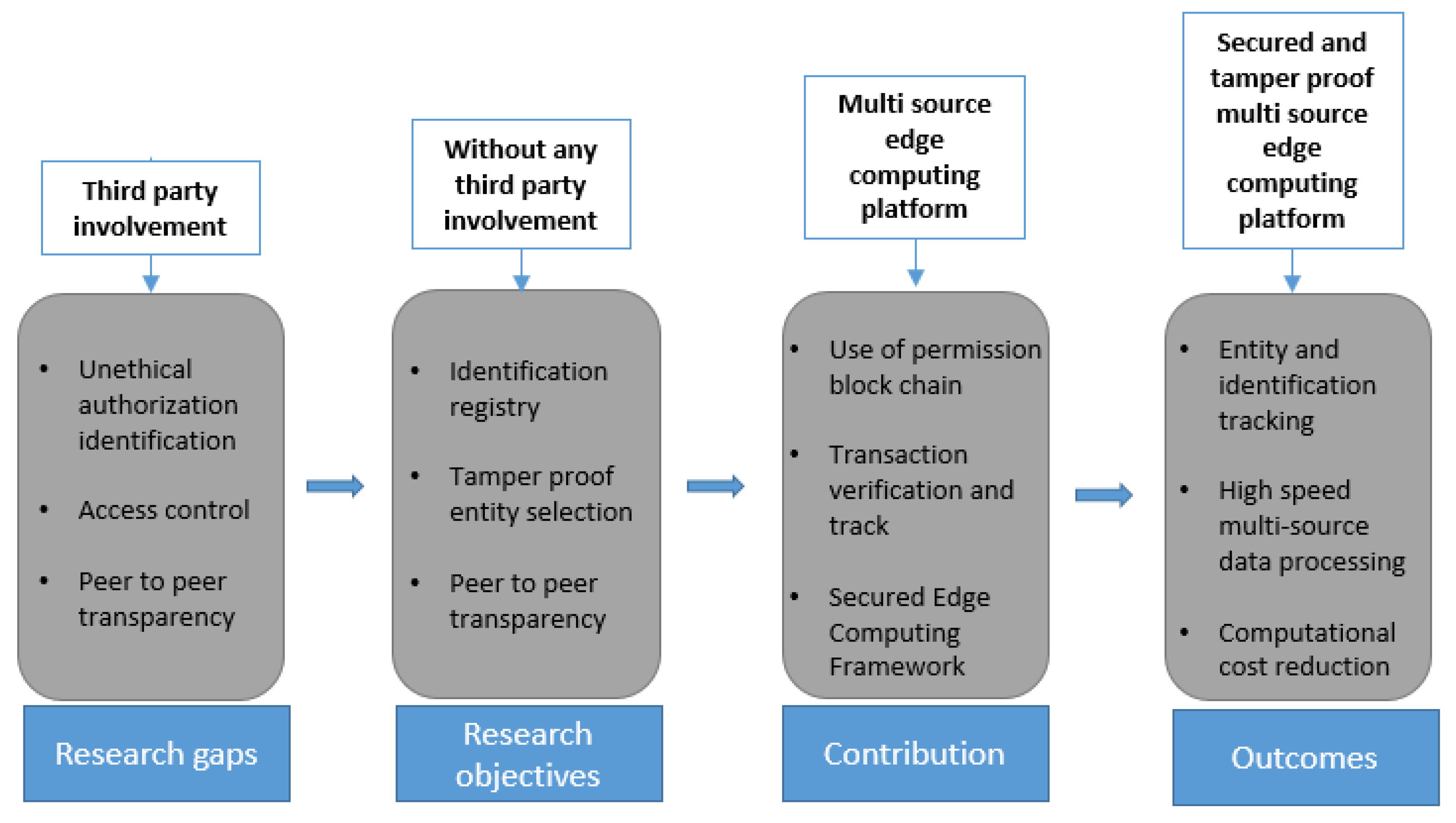
Sensors | Free Full-Text | BlockEdge: A Privacy-Aware Secured Edge Computing Framework Using Blockchain for Industry 4.0

Venkat Java Projects: - Java Ieee Projects List SN O Project Title Domain | PDF | Internet Of Things | Data Mining

A novel method for digital image copy-move forgery detection and localization using evolving cellular automata and local binary patterns | SpringerLink
Diverse examples of probabilistic automata, including the automaton... | Download Scientific Diagram
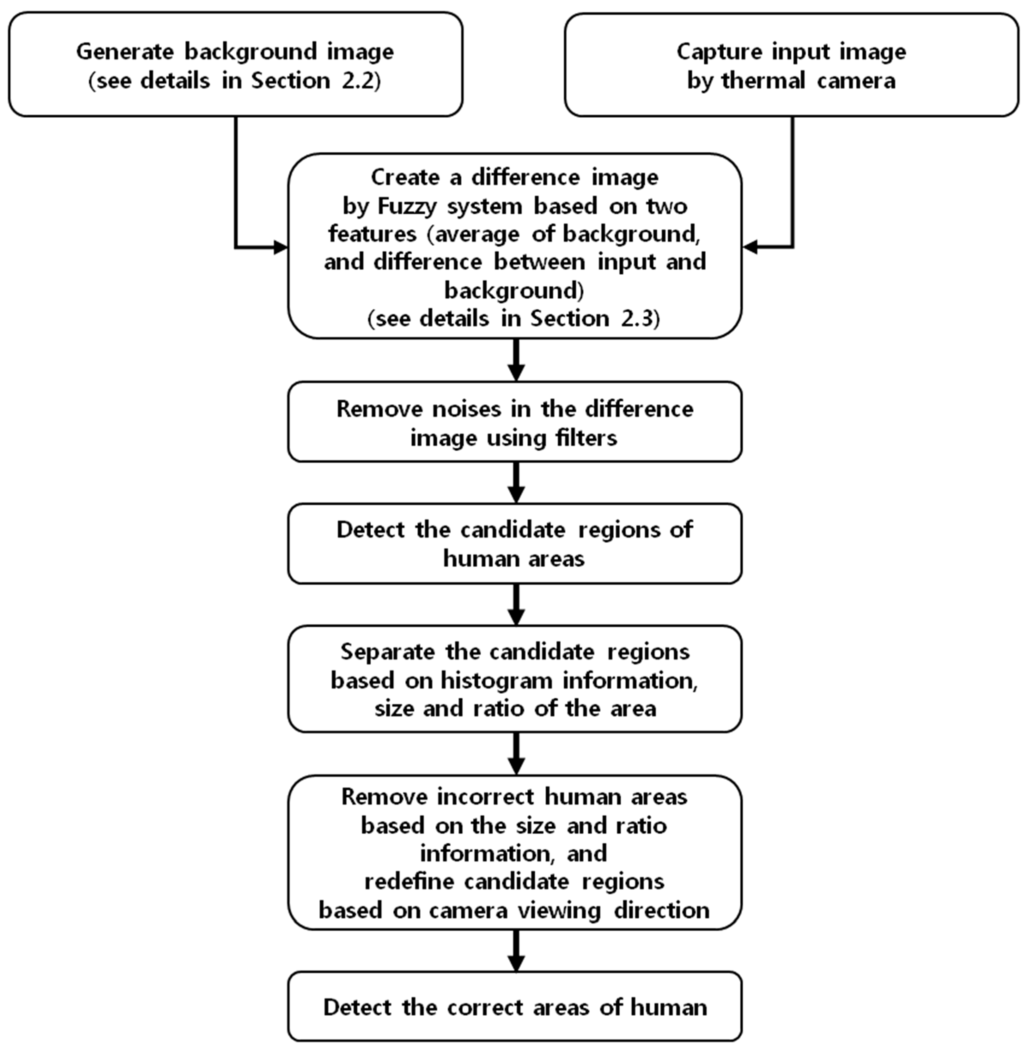
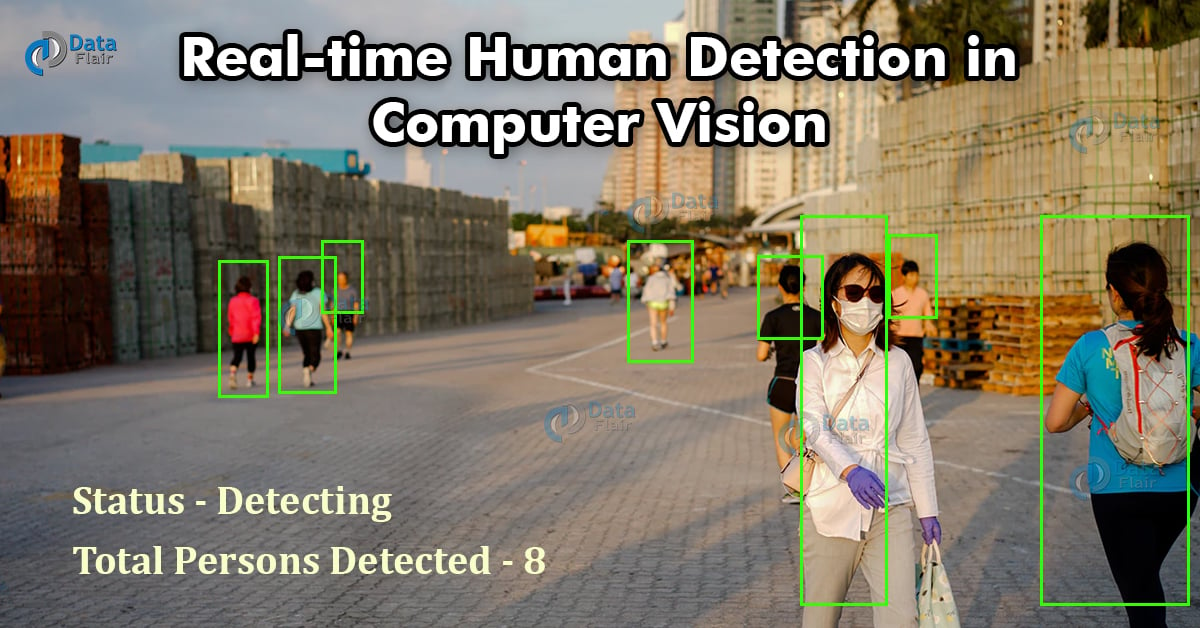
Sensors | Free Full-Text | Human Detection Based on the Generation of a Background Image and Fuzzy System by Using a Thermal Camera
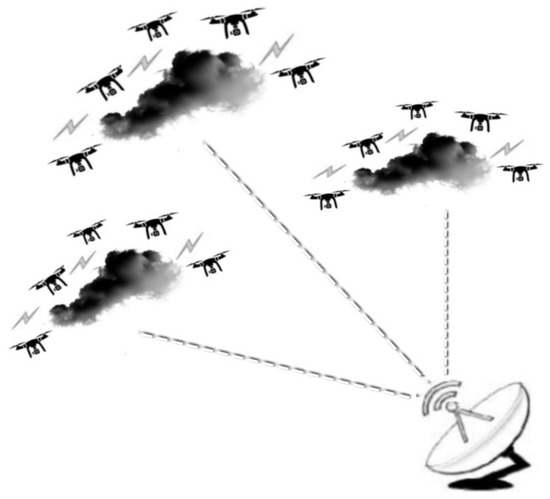
Drones | Free Full-Text | An Intrusion Detection System for Drone Swarming Utilizing Timed Probabilistic Automata
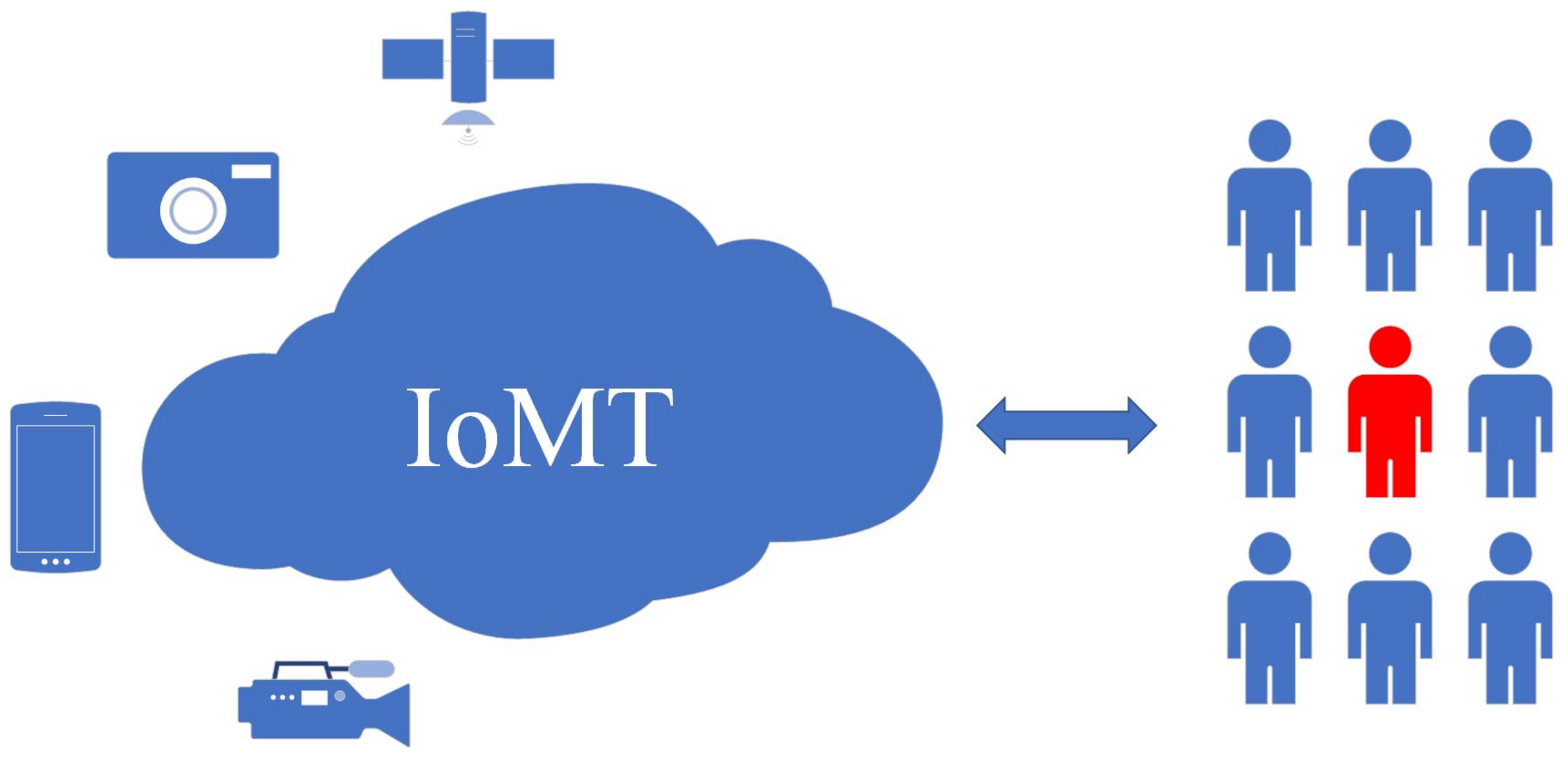
Sensors | Free Full-Text | GAN-Based Differential Private Image Privacy Protection Framework for the Internet of Multimedia Things